-
Nessus Crack카테고리 없음 2020. 3. 2. 04:13
Nessus 8.6.0 Crack With Activation Code LatestNessus Crack with Activation Code gives complete and very useful network vulnerability scanner for quick and easy patching, configuration as well as compliance auditingNessus Crack the centaur, searched for a vulnerability in Deianeira and exploited it to serve his goal, while Nessus, the program, does the same thing for computer networks, leaving aside the exploiting part of the legend.On the contrary, Nessus Activation Code does what it takes to keep exploiters at bay by patching the vulnerabilities found in the system. Its plugin library holds tens of thousands of items for you to add the the core application in order to make it your way, to match your expectations and preferences in the most simple, elegant, possible and, why not, plausible way.Nessus License Key can be used in small companies as well as in larger ones as its scalability is not limited to a specific number of networks, servers and workstations. Its integrated technologies help you perform physical as well as virtual device discoveries alongside software auditing.Furthermore, Nessus Registration Code also audits mobile devices in order to provide a broad asset coverage and profiling of the entire organization environment, both cable-depending and wireless-enabled hardware. You can now rest assured that you have an application to detect suspicious behavior or known malware such as botnets.All in all, Nessus Keygen adds a few layers of protection to your network by providing solutions to potential vulnerabilities, categorizes them, prioritizes them while also performing non-intrusive sensitive content auditing for better management and faster patching of the most important problems.FEATURES. A complete analysis of your security level. Up-to-date security vulnerability database.
Nessus Crack
We mostly focus on the developement of security checks for recent security holes. Our security checks database is updated on a daily basis, and all the newest security checks are available here and can be retrieved with the command nessus-update-plugins. An RSS feed of all the newest security checks allows you to monitor which plugins are added and when. Remote and local security. Traditional network security scanners tend to focus on the services listening on the network – and only on these. Now that viruses and worms are propagating thanks to flaws in mail clients or web browsers, this conception of security is getting outdated. Elegant architecture.
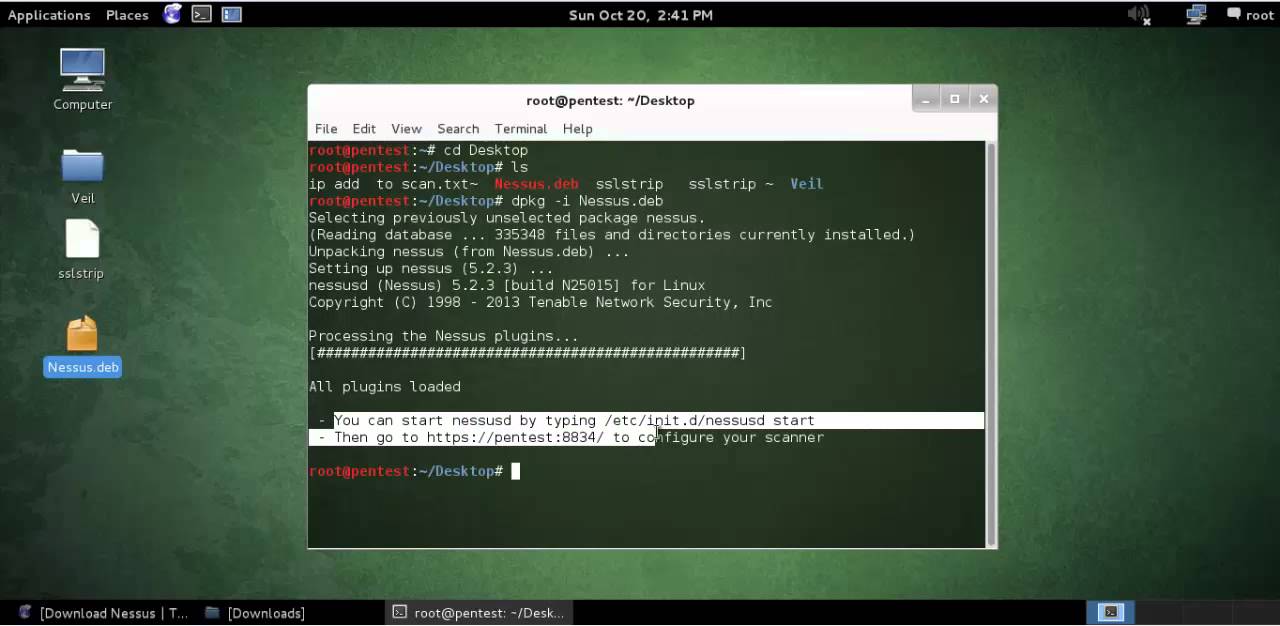
Extremely scalable. Nessus has been built so that it can easily scale down to a single CPU computer with low memory to a quad-CPUs monster with gigabytes of RAM. The more power you give to Nessus, the quicker it will scan your network. Plug-ins. Each security test is written as an external plugin, written in NASL.
This means that updating Nessus does not involve downloading untrusted binaries from the internet. Each NASL plugin can be read and modified, to better understand the results of a Nessus report. NASL. The Nessus Security Scanner includes NASL, (Nessus Attack Scripting Language) a language designed to write security test easily and quickly. NASL plugins run in a contained environment on top of a virtual machine, thus making Nessus an extremely secure scanner. Others.
Smart service recognition. Nessus does not believe that the target hosts will respect the IANA assigned port numbers. This means that it will recognize a FTP server running on a non-standard port (ie: 31337), or a web server running on port 8080. Nessus is the first scanner on the market to have implemented this feature for all the security checks (and has been copied by many since then). Multiples services. If a host runs the same service twice or more, Nessus will test all of them.
Nessus Crack Key

Nessus+crack+free Download
Believe it or not, several scanners on the market still consider that a host can only run one server type at once. Full SSL support. Nessus has the ability to test SSLized services such as https, smtps, imaps, and more. You can even supply Nessus with a certificate so that it can integrates into a PKI-fied environement.
Once again, Nessus was one of the first security scanner on the market to provide this feature. Non-destructive or thorough. Nessus gives you the choice between performing a regular non-destructive security audit on a routinely basis, or to throw everything you can at a remote host to see how will it withstands attacks from intruders.
Old Nessus VersionsAs Nessus is the name of the centaur that tricked Heracles’ wife into killing him in the Greek mythology, you can sense a similarity between the mythic creature and the software.Nessus, the centaur, searched for a vulnerability in Deianeira and exploited it to serve his goal, while Nessus, the program, does the same thing for computer networks, leaving aside the exploiting part of the legend.On the contrary, Nessus does what it takes to keep exploiters at bay by patching the vulnerabilities found in the system. Its plugin library holds tens of thousands of items for you to add the the core application in order to make it your way, to match your expectations and preferences in the most simple, elegant, possible and, why not, plausible way.Nessus can be used in small companies as well as in larger ones as its scalability is not limited to a specific number of networks, servers and workstations. Its integrated technologies help you perform physical as well as virtual device discoveries alongside software auditing.Furthermore, Nessus also audits mobile devices in order to provide a broad asset coverage and profiling of the entire organization environment, both cable-depending and wireless-enabled hardware. You can now rest assured that you have an application to detect suspicious behavior or known malware such as botnets.All in all, Nessus adds a few layers of protection to your network by providing solutions to potential vulnerabilities, categorizes them, prioritizes them while also performing non-intrusive sensitive content auditing for better management and faster patching of the most important problems.File Size: 92.2 MBDownloads: 50520Added: November 5 2019User rating: 3.5.